Fusing Digital Identities and Web3: Why We Need a Reboot

With over 5.4 billion internet users worldwide, protecting digital identities is becoming increasingly important. According to the Consumer Sentinel Network of the Federal Trade Commission — an extensive database that records consumer complaints and cases of fraud in the USA — 19% of over 5 million consumer complaints in 2023 involved identity theft, a clear wake-up call for better security measures.
Centralized identity management systems, which are easily vulnerable and deprive users of control over their data, are increasingly giving way to decentralized, user-centric systems. These not only offer greater security but also give users control over their own information paving the path towards a safer digital future.
Security Gaps in the Digital Age: The Centralized Data Dilemma
Securing personal information is one of the most important concerns of our digital age, yet traditional data management practices are vulnerable to a variety of cyber threats.
Traditionally, individuals’ personal details are kept within a web of centralized databases. This model, characterized by its reliance on a singular entity or platform for identity verification and data management, inherently exposes users to a variety of cyber threats. Breaches, hacks, and unauthorized data exploitation loom as ever-present dangers, underscoring a critical flaw in the system: a compromise to privacy and security that also undermines user autonomy.
Currently, centralized identity management systems — notably those of Big Tech behemoths like Meta and Google — operate under a paradigm that accumulates and controls user data within their vast digital fortresses. Besides stripping individuals of the control over their own data, the concentration of sensitive information also amplifies the risks tied to single points of failure. This makes the need for a solution that prioritizes security all the more urgent.
Advancing Digital Identity Standards
The invention of Decentralized Identifiers (DIDs) marks a paradigm shift towards user-centric digital identities that rectify the inherent vulnerabilities of centralized identity management systems.
- DIDs are a type of digital identity that individuals can use to prove who they are online without relying on a central authority like a government or a large corporation, giving users full control over their own identity.
- They allow users to use the same identity across different services and platforms without needing to repeatedly provide personal details. Only explicitly authorized data can be used by platforms.
- DIDs work by creating a unique, cryptographically secure identifier for each user and recording it on a blockchain. This identifier is linked to a DID document that contains the public keys, authentication protocols, and service endpoints required to interact securely with the identity.
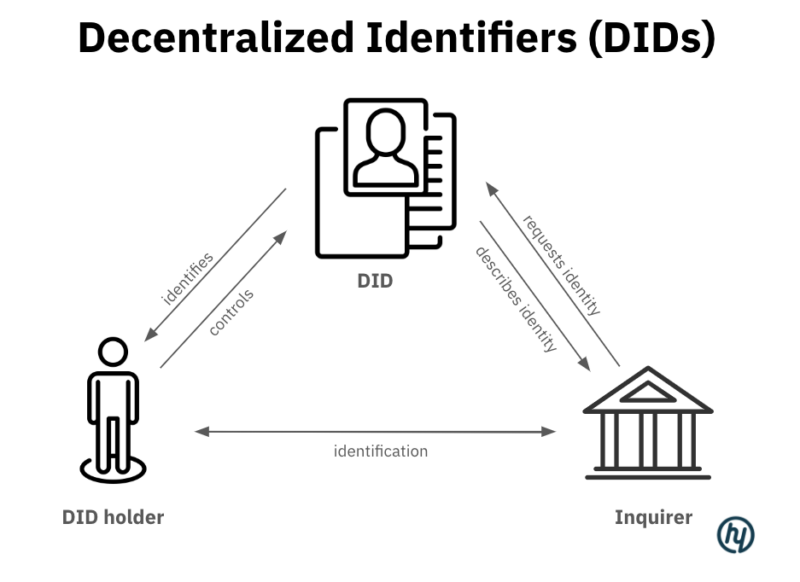
The endorsement of DID standards by the World Wide Web Consortium (W3C) is a watershed moment for the global standardization of digital identities, recognizing the value of universal and interoperable digital identity frameworks. By adopting DID standards, the digital sphere moves closer to a future where individuals can effortlessly verify their identity across various platforms and services, without compromising their privacy or security. The implications of such a standardized digital identity framework are profound. It promises more seamless online experiences, enhanced privacy protections, and a reduction in online identity theft and fraud. To the benefit of internet users all around the world, the momentum behind these developments signals a collective effort to reimagine digital identity security.
Web3 as a Solution
Blockchain’s inherent features — immutability, transparency, and decentralization — offer a robust framework whereby digital identities are no longer mere data points within centralized repositories, but assets securely controlled by the individuals behind them. This fundamentally alters the landscape of privacy and security in the digital domain, enabling a mode that shields personal information from unauthorized access while allowing for it to be selectively shared on the individual’s terms.
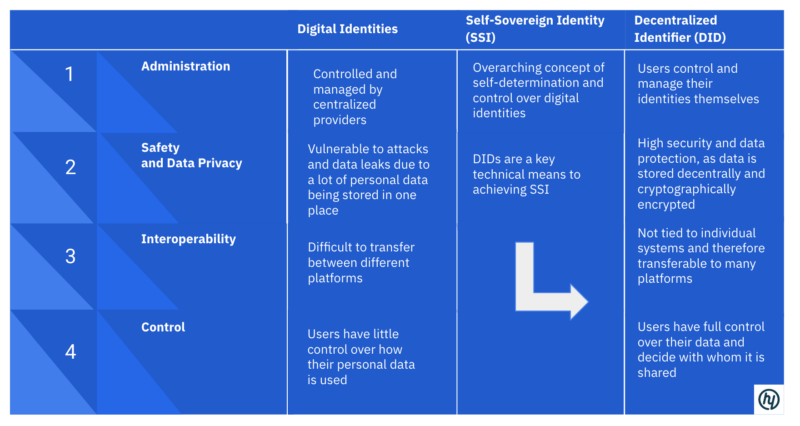
DIDs and Systems for Self-Sovereign Identity (SSI) are at the heart of this transformation. While DIDs enable unprecedented platform interoperability, SSIs allow individuals to store their identity credentials in secure digital wallets. These wallets empower users to practice selective disclosure (i.e. sharing information based on consent protocols that they control, only as needed).
Leveraging blockchain-based DIDs and SSIs addresses longstanding challenges in digital identity verification, most notably identity theft and fraud. By decentralizing the storage and management of personal data, blockchain minimizes the risk of centralized data breaches. Additionally, blockchain’s auditability further bolsters security by ensuring that any access or changes to a user’s digital identity are transparent and traceable.
The evolution towards a Web3-based digital identity framework also opens up new avenues for digital interactions and transactions. Enhanced privacy and security measures allow users to engage in online activities, from accessing services to executing contracts, with greater confidence. In general, a digital economy with trust built into its system facilitates more seamless and safer exchanges between parties.
Harnessing Decentralized Identities: Use Cases and Business Models
During this year’s hy Web3 Summit, Ingo Rübe, founder of the Kilt Protocol, explored the use cases and opportunities emerging from decentralized identity solutions. Kilt Protocol is a blockchain-based platform designed to enable users to claim, verify, and manage their digital identities independently.
Spoiler: the many use cases of DIDs are truly disruptive.
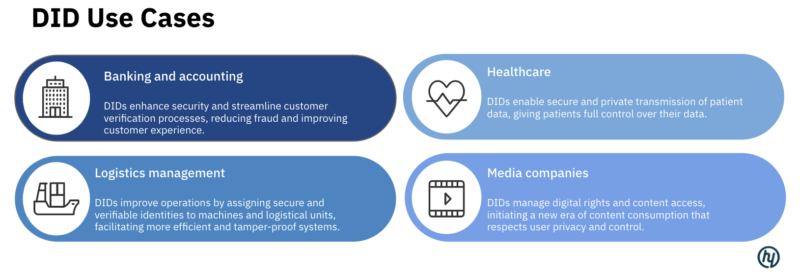
Real-world examples of how DIDs can improve business operations already exist — let’s take a look at the case of KILT x Hapag-Lloyd x Deloitte x Vodafone: International shipping expert Hapag-Lloyd and telecommunications giant Vodafone are already embracing Deloitte’s public blockchain solution for the identification and tracking of shipping containers. The initiative involves a combination of Deloitte’s KYX platform (which integrates know your customer (KYC) and know your cargo principles) and an Internet of Things (IoT) device, which is attached to containers to digitize and streamline supply chain operations. Each container is given its own digital identity and sensors measure key figures such as weight, temperature and location. In addition to increasing efficiency and transparency, this can also put a stop to theft, drug trafficking across borders and the transport of illegal objects.
The difference to previous major logistics projects (such as Maersk x IBM) is that the use case is very clearly defined. The participants and process chain are clearly delineated and the technology therefore ensures greater security and efficiency gains in container logistics in the shortest possible time.
Conclusion: The Future is Now
The transition to decentralized, user-centric solutions marks the beginning of a new era in which individuals regain control over their digital identities and machines and objects are gradually given their own “identities”. In this era, digital ecosystems are more secure, transparent, automated and inclusive – with privacy, security and autonomy taking center stage.


